Blog
May 30, 2025
PHP exploitations and web application security breaches are very present, very expensive threats in the modern digital landscape. With the cost of breaches continuing to climb and having ramifications that go far beyond financial penalties and fees, your team must seriously contemplate the question – can you afford to risk PHP exploitation in your applications?
In this blog, I go through the realities of what a web application security breach can cost your business. I then outline common types of PHP exploitation to guard against, and I provide solutions for teams looking to improve their PHP application security strategies and stop breaches before they occur.
What Does PHP Exploitation Cost Your Business?
The financial, operational, and reputational impact of PHP exploitation cannot be overstated. Even a single incident can trigger a cascade of expenses that will take months, even years, to pay down. These can include, but are not limited to, legal fees, compliance penalties, lost revenue due to application downtime, and compromised customer trust.
Financial Fees and Penalties After PHP Exploitation
According to IBM, the average cost of a data breach in 2024 was $4.88 million.
A PHP web application security breach is costly for businesses, often in ways that aren’t immediately obvious.
After successful PHP exploitation, your team may need to hire cybersecurity experts to investigate the size, cause, and impact of the breach. Depending on the complexity of your application and how many apps were affected, these services can cost tens or even hundreds of thousands of dollars.
If your applications handle personal or sensitive data, you must also comply with data protection laws. For example, under GDPR, a PHP exploitation could result in steep fines, such as up to €20 million or 4% of global turnover.
Additional costs can include lawsuits from users, higher insurance premiums, lost future revenue, reduced productivity, recovery expenses, and more.
Learn More About PHP GDPR Standards
The Cost of Downtime After a Web Application Security Breach
One hour of downtime costs $300,000 on average, according to the New Relic 2024 State of Observability Report.
When critical applications go down due to PHP exploitation or response efforts, the effects can ripple across your organization. Whether downtime lasts minutes or hours, it seriously impacts customer experience, alongside your revenue, operations, and reputation.
This is especially true for customer-facing applications like e-commerce platforms, PHP finance applications, or booking systems, where every moment offline means lost income. For high-traffic or high-value applications, PHP exploitation and recovery quickly adds up to thousands or even millions in lost transactions.
If your business has service-level agreements (SLAs), downtime can also lead to contractual penalties, such as issuing service credits, refunds, or free extensions, all of which affect your bottom line. Customer support can also be overwhelmed as users seek immediate solutions.
For hosting providers and shared hosting environments, the impact of PHP exploitation multiplies, affecting countless applications across numerous businesses. With so many applications hosted, the consequences can be widespread, costly, and long-lasting.
PHP Exploitation Results in Reputational Damage and Loss of Customer Confidence
A single PHP exploitation incident can destroy years of brand-building within hours. In today’s global and connected world, trust is currency, and the impact of a web application security breach extends well beyond financial losses. With news spreading fast, you may struggle to control the fallout. Your customers might:
- Lose All Faith in Your Business – Users expect businesses to protect their personal data. A web application security breach, regardless of the cause, signals a failure to meet that expectation. Your customer base will hold you accountable for any damages, and that trust and confidence in your reliability may take years to regain...if you can ever regain it at all.
- Turn to Competitors – In competitive markets, rivals may highlight your breach to position themselves as safer alternatives.
- Learn About the Breach Through Social Media or News – Bad news travels quickly. A major breach impacting many customers can trigger negative press, backlash, and damaging reviews.
Once your reputation is compromised, rebuilding it can take significant time and resources. For instance, according to a recent report by Splunk, companies spend on average $14 million to repair their reputations through brand trust campaigns. An additional $13 million goes to increasing programs for public, investor, and government relations.
Back to topTypes of PHP Web Application Security Breaches
With PHP powering an estimated 75% of web applications, it’s no surprise that malicious attacks and security risks take many forms. While the list of potential threats for breaches is long, there are a few types of PHP web application security breaches – such as remote code execution, SQL injection, and others – that are common tools used for PHP exploitation.
For any application, leaving these vulnerabilities unaddressed is particularly dangerous; however the risk becomes much larger in shared hosting environments. In that context, PHP exploitation has the potential to impact multiple customers, expose customer data to one another, and cause other damaging consequences.
Prevent a Web Application Security Breach With These Tips
Are you guarded against the most prevalent PHP vulnerabilities? Join Zend for an on-demand expert webinar giving an overview of how to tackle the most common PHP security risks at scale.
Remote Code Execution (RCE)
RCE happens when an attacker runs malicious code on a remote machine via a public or private network. It is one of the most dangerous PHP exploits, often leading to a fully compromised system. Unlike cross-site scripting (XSS) or cross-site forgery (CSRF), RCE doesn’t need user interaction and can cause immediate, severe consequences, such as:
- Full Server Takeovers – Attackers with admin privileges can modify content, steal data, or deploy ransomware.
- Credential Theft – Environment variables, database credentials, and config files can be exposed.
- Malware Installation – Attackers may install web shells for persistent access.
- Compliance Violations – Exposed sensitive data can trigger GDPR, HIPAA, or other regulatory breaches.
RCE exploits a variety of PHP vulnerabilities, so mitigation requires a multi-pronged approach, including input sanitization, secure memory management, and access controls.
SQL Injection
SQL injection occurs when data or statements are inserted into an SQL query. It's a common form of PHP exploitation that can give attackers access to databases or even full system control. SQL injection works by exploiting poorly handled input. When user-provided data is added to an SQL query without proper sanitization, attackers can inject malicious SQL code.
Consider this example:
// Vulnerable code
$username = $_GET['user'];
$query = "SELECT * FROM users WHERE username = '$username'";
$result = mysqli_query($conn, $query);If the attacker enters user=admin' --, the resulting query becomes:
SELECT * FROM users WHERE username = 'admin' --'In this case, the -- is a comment in SQL, which effectively nullifies the rest of the query. This allows the attacker to manipulate results in order to possibly bypass login systems, access sensitive data, modify or delete database content, extract entire databases, and much more.
File Inclusion Vulnerabilities
File inclusion vulnerabilities are security flaws in PHP web applications that let attackers include and execute arbitrary files on a server. These can lead to data leaks, code execution, and server compromises—especially in shared hosting environments.
There are two main types of file inclusion vulnerabilities:
- Local File Inclusion (LFI) – The attacker includes files already on the server, such as
/etc/passwd,.htaccess, or PHP session files. - Remote File Inclusion (RFI) – The attacker includes files from a remote server, injecting malicious code into the application.
Both LFI and RFI are serious threats, especially in shared hosting setups where multiple apps run on the same server. An attacker gaining access to one app can expand their attack to others.
Session Hijacking
Session hijacking is a cyberattack where a malicious actor takes control of a user’s web session by stealing or manipulating the session token, a unique identifier for communication between the user and a website. Common ways to intercept session tokens include network eavesdropping, phishing, and exploiting unaddressed vulnerabilities. Once an attacker steals the token, they can impersonate the user and gain unauthorized access to sensitive data or services.
Techniques for session hijacking vary but include methods like session sniffing (monitoring network traffic to capture tokens), XSS (injecting malicious scripts to steal cookies), and session fixation (forcing a user to use a compromised session ID).
Preventing these attacks requires secure session management, encrypted network communication, and educating users about phishing tactics.
Back to topHow to Prevent PHP Exploitation and Web Application Security Breaches
The best defense is a good offense, and your first strategy to address PHP exploitation and avoid the associated costs is to ensure that exploitation cannot occur in the first place. It is critical for your team to take steps to safeguard your applications. Failure to do so will turn PHP exploitation planning from an if to a when.
Use the Most Up-to-Date PHP Versions
The best way to prevent web application security breaches is by using the latest version of PHP. This ensures you have the most current security patches and features to protect against PHP exploitation.
With new vulnerabilities emerging daily, outdated or unpatched PHP leaves your business exposed. That being said, the PHP release cycle moves fast, with new feature releases occurring every year. For many teams, upgrading quickly isn’t always feasible. In such cases, contracting a third party for PHP long-term support (LTS) is the best solution.
For example, Zend PHP LTS extends the lifespan of your PHP version by at least two years beyond community support. This gives you time to plan upgrades, implement those upgrades on your schedule, maintain compliance, and stay secure against evolving threats.
Stay Secure With Zend PHP LTS
Upgrade on your schedule with Zend PHP LTS, which provides enterprise-grade support two years beyond the community support lifecycle. Learn more about our LTS offering and Migration Support via the buttons below.
Address Newly Identified CVEs
Common Vulnerabilities and Exposures (CVEs) are PHP security flaws that have been identified, publicly shared, and assigned an ID. These flaws are discovered by the PHP community and third parties, with new CVEs found daily.
Once public, mitigations are provided through sources like the Zend PHP Security Center, which helps teams apply or backport security patches while planning long-term fixes. When needed, we also provide code workarounds within specific CVE entries to address threats immediately.
Regularly checking for new CVEs is an effective way to prevent security breaches, and addressing CVEs promptly helps protect against costly financial and reputational damage.
Learn more about CVEs and Common PHP Vulnerabilities
Containerize PHP Applications
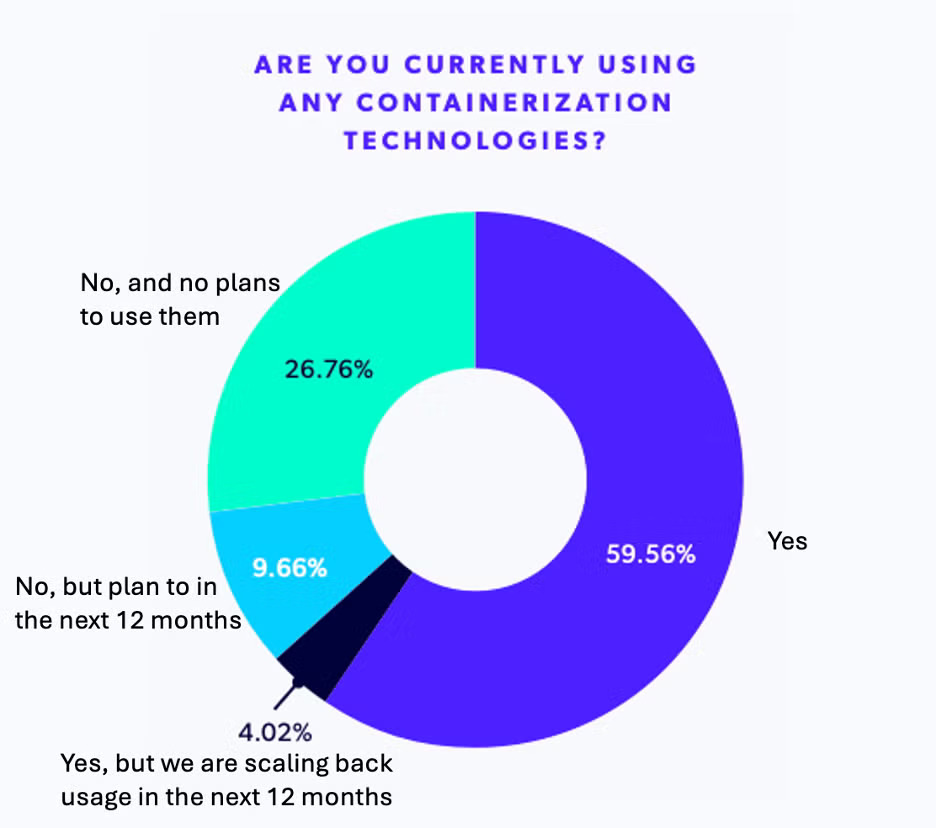
Source - 2025 PHP Landscape Report
According to the 2025 PHP Landscape Report, nearly 60% of surveyed PHP professionals currently utilize container technologies, with approximately 10% planning to implement containers within the next 12 months. This popularity comes as no surprise, as containers play a vital role in improving PHP application security by creating isolated environments that prevent interference between systems.
This isolation ensures that each system operates independently, significantly reducing the risk of cross-contamination in the event of a web application security breach. Furthermore, containers control the application’s access to system resources, limiting the impact of potential PHP exploitation by reducing the attack surface.
Learn more about How PHP Containers Improve Application Security
Outsource Support to Proven Experts
Keeping up with evolving PHP security best practices is a heavy lift for any team, particularly if you’re working with limited developers and balancing the drive to create new features that grow your business. However, security is never optional, and investing in a rigorous protocol now can save you potential millions.
One solution is to partner with an experienced third-party team of PHP experts, such as Zend. We deliver the advanced security and compliance solutions you need to avoid PHP exploitation and safeguard against potential web application security breaches. In addition to our PHP LTS and Migration Services, we also offer:
- Hardened Docker Images compliant with CIS Docker Benchmarks v1.6.0
- A full suite of Professional Services to match your project’s needs
- Flexible Black Belt Service Hours to discover and diagnose gaps in your PHP security
- Continuous performance and health monitoring with Zend Admin as a Service
- Consultative Guidance to train and prepare your team to tackle PHP exploitation and attacks
- Secure and supported runtimes through ZendPHP
- And much more.
When you’re ready to get started, reach out and contact us today. A Zend PHP expert will be in touch to discuss your application, business, and goals.
Zend Makes Mission-Critical PHP Possible
ZendPHP runtimes, when paired with ZendHQ observability and orchestration tooling, deliver the building blocks for secure and scalable web applications. Try them free for 21 days to see how they fit in your infrastructure.
